1. Legal status is confimed
Article 21 of the Cybersecurity Law of the People's Republic of China stipulates that "the state implements the cybersecurity classified protection system", and requires that "the network operator shall fulfill the obligation of security protection according to the requirements of the cybersecurity classified protection system"; Article 31 stipulates that "key protection shall be implemented for the national critical information infrastructure on the basis of the cybersecurity classified protection system".
2. Protection object is expanding
As new technologies such as cloud computing, mobile interconnection, big data, internet of things, artificial intelligence and so on are developing rapidly, the concept of Computer Information System is outdated, especially the development of internet highlights the value of big data, so the protection object will be expanded continuously
3.Trusted Computing is enhanced
he 2.0 Era of Classified Protection establish a core technical system for classified protection system based on the trusted computing technology, which strengthens the critical concept of trusted sytem.
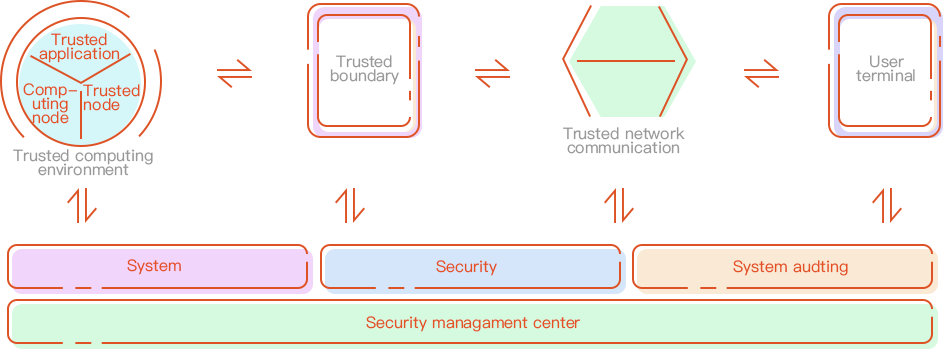
4. Changes in General Requirements
General requirements include security general requirements, cloud computing security extension requirements, mobile interconnection security extension requirements, Internet of Things security extension requirements, and industrial control systems security extension requirements.
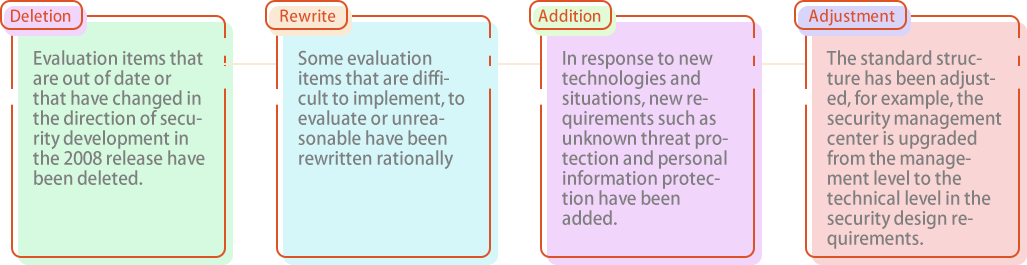
The core of general requirements in the 2.0 era of classified protection is optimization.
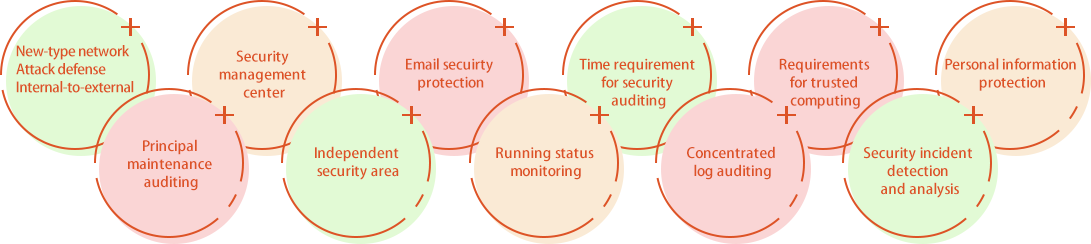
Key contents added
5. Changes in Extension Requirement
(1)Security extension requirement of cloud computing platform
+ Responsible body is divided into two: cloud service provider and cloud tenant
+ Classified protection level matches
Cloud computing platform‘s protection level should be determined independently
Cloud computing platform needs to pass the classified protection level evaluation
Identical cloud computing platform can carry information system of different levels
Cloud computing platform cannot carry information system of higher levels
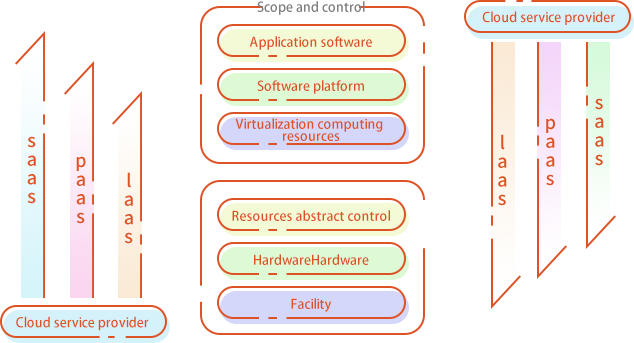
Cloud computing application scenario:
(2)Security extension requirement of Big Data
Large data with a uniform security responsibility unit should be classified as an whole object.。
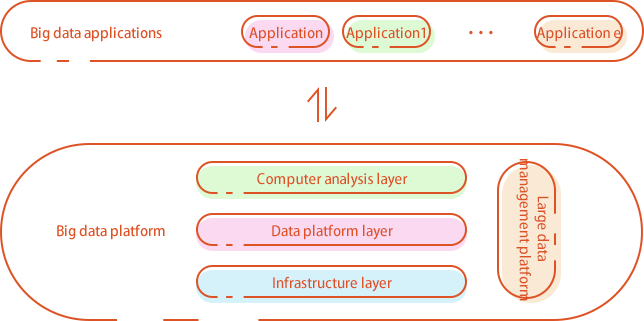
Large data system composition:
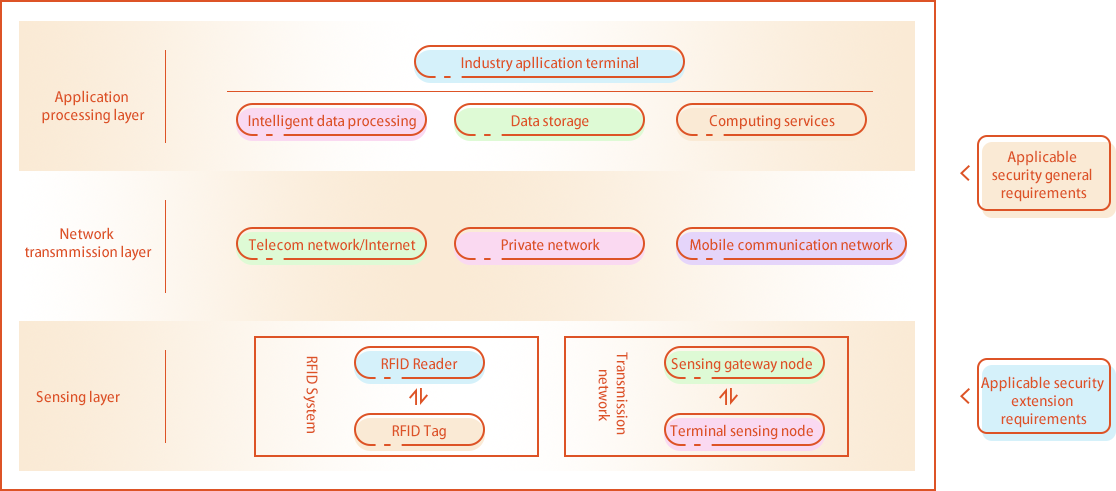
(3) Security extension requirement of IoT
The Internet of Things (IoT) should be classified as a whole object, which mainly includes perception layer, network transport layer and processing application layer.
(4)Security extension requirement of Mobile Interconnected Network
Classified protection object of mobile interconnection technology should be classified as a whole object, and the factors such as mobile terminal, mobile application and wireless network should not be classified separately, and the application environment and application object should be classified together with the classified protection object of mobile interconnection technology.
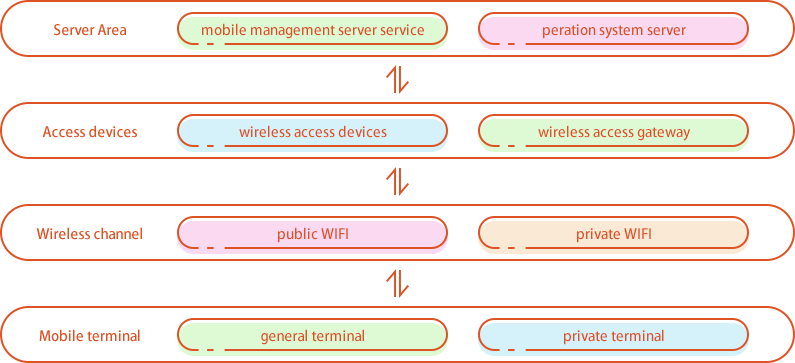
Mobile Internet application architecture
(5)Security extension requirement of Industrial Control System
Industrial control system is composed of production management layer, field equipment layer, field control layer and process monitoring layer. The device layer, the field control layer and the process monitoring layer shall be classified as a whole object, and the elements of each level should not be classified separately. For large-scale industrial control system, it can be divided into several objects according to system functions, control objects and manufacturers.
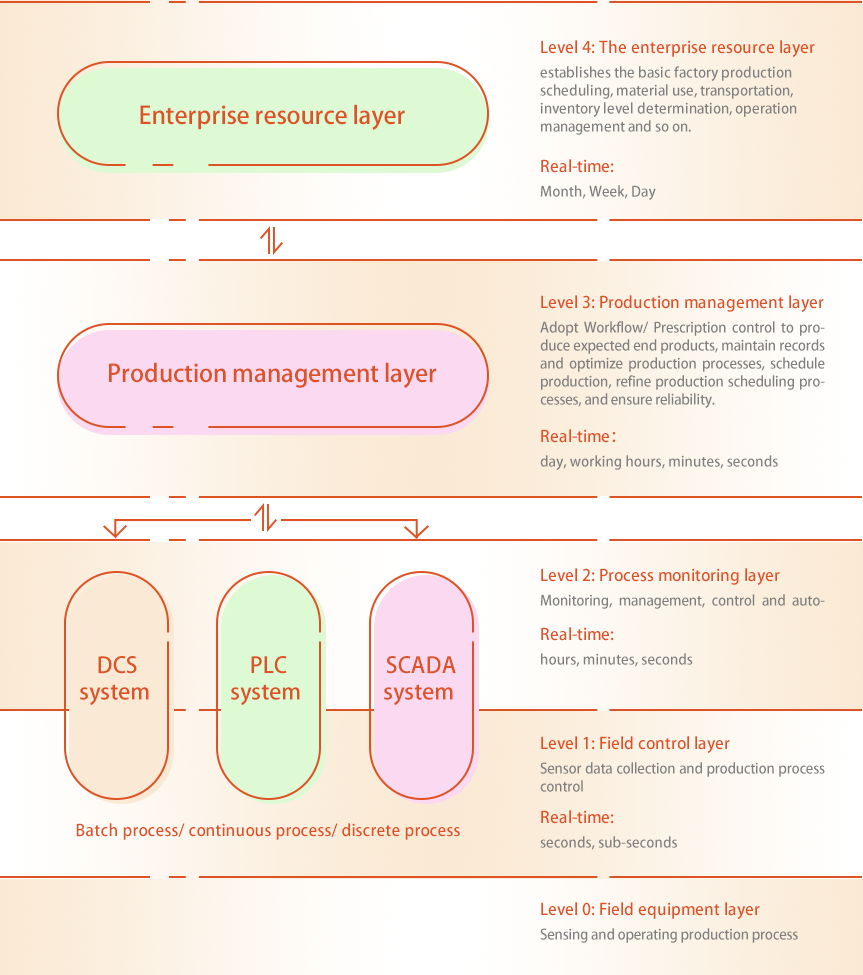
Note: This chart is a classic hierarchical model of industrial control system reference IEC62264-1, but as the industry 4.0 and information physics system develops rapidly, it can not be fully applicable, so for the actual development of different industries enterprises, partial hierarchical merger is allowed.
1. Legal status is confimed
Article 21 of the Cybersecurity Law of the People's Republic of China stipulates that "the state implements the cybersecurity classified protection system", and requires that "the network operator shall fulfill the obligation of security protection according to the requirements of the cybersecurity classified protection system"; Article 31 stipulates that "key protection shall be implemented for the national critical information infrastructure on the basis of the cybersecurity classified protection system".
2. Protection object is expanding
As new technologies such as cloud computing, mobile interconnection, big data, internet of things, artificial intelligence and so on are developing rapidly, the concept of Computer Information System is outdated, especially the development of internet highlights the value of big data, so the protection object will be expanded continuously
3.Trusted Computing is enhanced
he 2.0 Era of Classified Protection establish a core technical system for classified protection system based on the trusted computing technology, which strengthens the critical concept of trusted sytem.

4. Changes in General Requirements
General requirements include security general requirements, cloud computing security extension requirements, mobile interconnection security extension requirements, Internet of Things security extension requirements, and industrial control systems security extension requirements.
The core of general requirements in the 2.0 era of classified protection is optimization.

Key contents added

5. Changes in Extension Requirement
(1)Security extension requirement of cloud computing platform
+ Responsible body is divided into two: cloud service provider and cloud tenant
+ Classified protection level matches
Cloud computing platform‘s protection level should be determined independently
Cloud computing platform needs to pass the classified protection level evaluation
Identical cloud computing platform can carry information system of different levels
Cloud computing platform cannot carry information system of higher levels

Cloud computing application scenario:
(2)Security extension requirement of Big Data
Large data with a uniform security responsibility unit should be classified as an whole object.。

Large data system composition:
(3) Security extension requirement of IoT
The Internet of Things (IoT) should be classified as a whole object, which mainly includes perception layer, network transport layer and processing application layer.

(4)Security extension requirement of Mobile Interconnected Network
Classified protection object of mobile interconnection technology should be classified as a whole object, and the factors such as mobile terminal, mobile application and wireless network should not be classified separately, and the application environment and application object should be classified together with the classified protection object of mobile interconnection technology.

Mobile Internet application architecture
(5)Security extension requirement of Industrial Control System
Industrial control system is composed of production management layer, field equipment layer, field control layer and process monitoring layer. The device layer, the field control layer and the process monitoring layer shall be classified as a whole object, and the elements of each level should not be classified separately. For large-scale industrial control system, it can be divided into several objects according to system functions, control objects and manufacturers.

Note: This chart is a classic hierarchical model of industrial control system reference IEC62264-1, but as the industry 4.0 and information physics system develops rapidly, it can not be fully applicable, so for the actual development of different industries enterprises, partial hierarchical merger is allowed.











