Concept
“
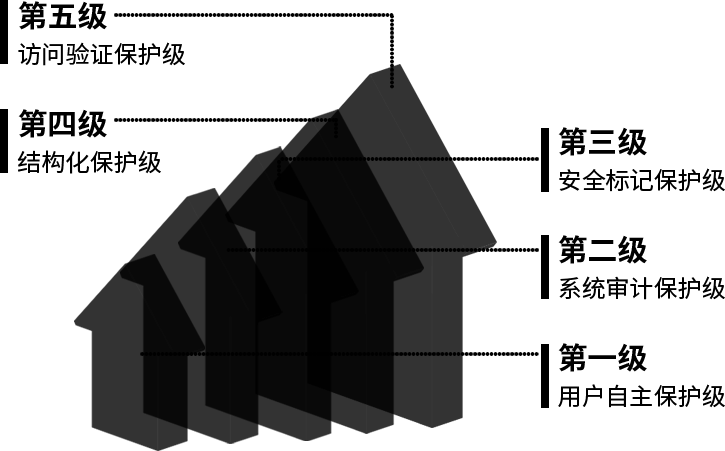
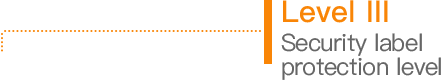
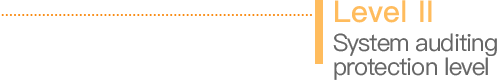
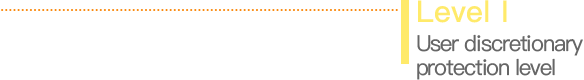
Cybersecurity classified protection refers to carrying out multilevel protection and supervision over network system (including information systems, data, applications, services), and implementing level-to-level administration for the network security products used in network, and responding to and resolving network security events and incidents.
Cybersecurity classified protection refers to carrying out multilevel protection and supervision over network system (including information systems, data, applications, services), and implementing level-to-level administration for the network security products used in network, and responding to and resolving network security events and incidents.